Network Resilience Risk Assessment
Condition Zebra’s Network Resilience Risk Assessment (NRA) is a value-driven and hands-on approach with years of experience that is designed to test whether your network infrastructure is resilient to a single point of failure (SPOF).
Following the Risk Management in Technology (RMiT) Guideline by Bank Negara Malaysia, there are a few items under clause S 10.33 – S 10.40 that we need to conform to.
Below is our network resilient assessment testing framework that conforms to the checklist but is not limited to.
a) Network Design Review Methodology
b) Network Device Review Methodology

Network Design Review Methodology
We will conduct Network Design Review – Interview session with the administrators on current network assets and control.
The set of exercises performed during the Network Design and Architecture Review assessment is illustrated below:
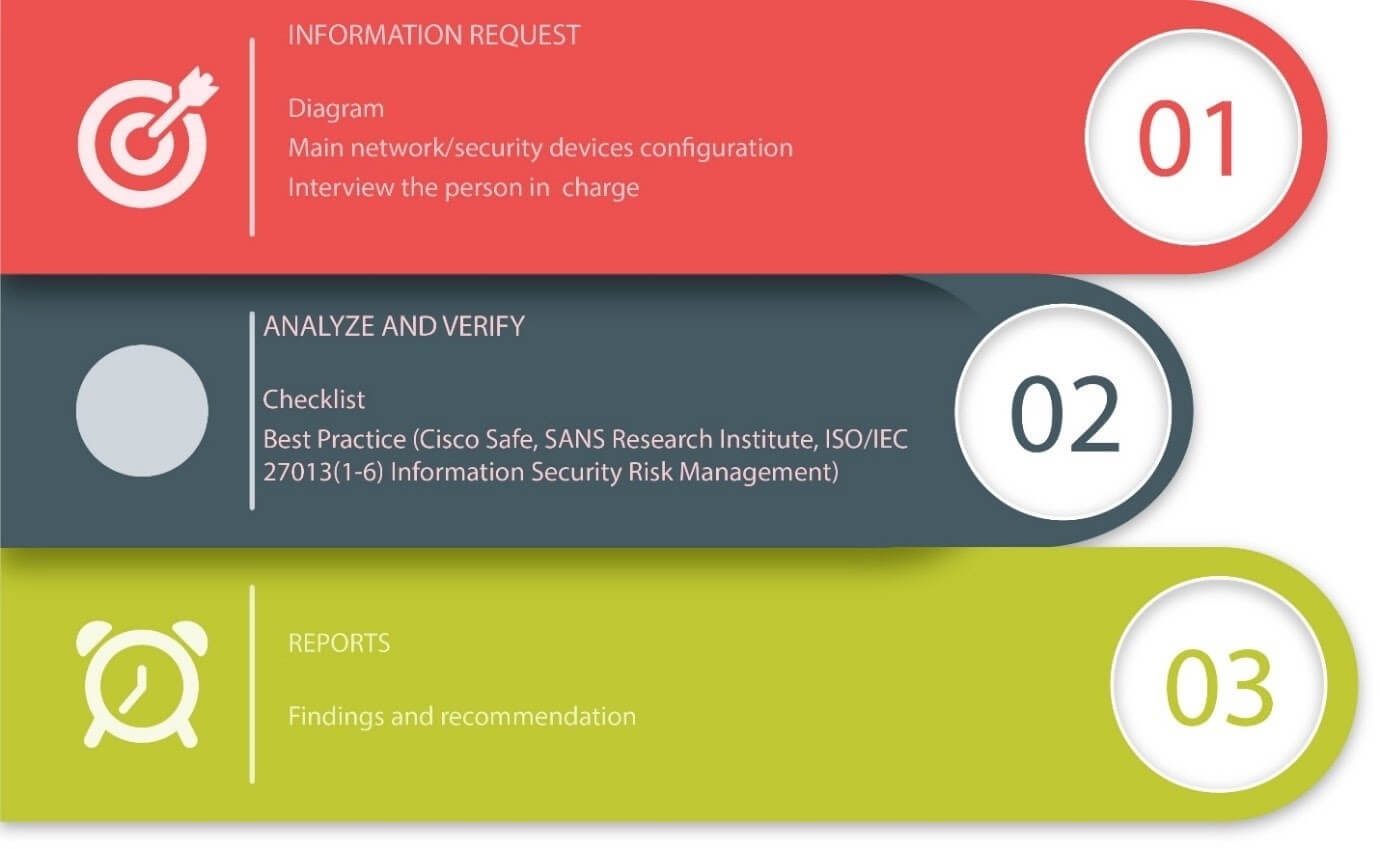
Information Request
We will gather network information such as network diagrams, device configurations, and other related documents. For this, we will need to identify and interview the key person responsible who can give us all the required information.
Lastly, we will also review the current network monitoring system, network security controls & collection and archiving of network device logs.
Analyze and Verify
Review the network diagram and device configurations based on the checklist that is created from several industry best practices like Cisco Safe, SANS Research Institute, National Institute of Standards and Technology (NIST), ISO/IEC 27013(1-6) Information Security Risk Management and CIS control 12 & 13.
Report
Prepare a report for findings and recommendations related to the previous activities.
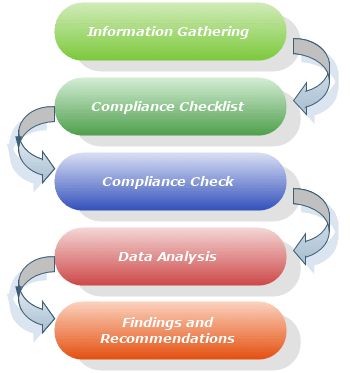
Network Device Review Methodology
Network Device Review is performed to determines network devices are in good configuration and do not have any flaw that can be exploited by the attacker. The review includes activities such as review current configuration files of network devices such as router and core switch as well as security devices such as firewall and IPS.
The objective of this assessment is to identify any weaknesses of the current configuration of devices involved and proposed it for improvement to meet security standards or device best practices.
The activity will be conducted by following these stages as below:
Information Gathering
In this process, the scope covers reviewing and determine network devices that have been agreed in the Scope of Services earlier before the assignment is conducted. The information of the network device such as the devices name, type, and IP address also need to be determined. During this process, it is important to have a copy of the current configuration’s file of the determined network device in a hard copy or soft copy in order to review the current configuration of the network device.
Compliance Checklist
An in-house compliance checklist will be used. The in-house compliance checklist has been formed by following the industry best practice standard. However, under circumstances, an automated tool might be used to replace the compliance checklist to audit the network device. A different compliance checklist will be used for different network devices type.
Compliance Check
At this stage, a compliance check or gap analysis is performed between the current configuration settings of the network device with the in-house compliance checklist.
Data Analysis
All data gathered during the assessment will be compared and analyzed against industry security best practices.
Findings and Recommendations
This process involves the presentation of results of data analysis, list of identified security misconfigurations, and consolidates recommendation/rectification, report and presentation.