Secure SDLC Free eBook
Secure Software Development is a complex topic. We break this down into
an easy and digestible guide that’s important for your needs:
⇒ Introduction to Software Development Lifecycle (SDLC)
⇒ The Basics of Secure SDLC
⇒ How to be successful in your Secure Software Development
⇒ Overview of OWASP top 10 software security vulnerabilities
Download today and start learning with our guide.
6 Phases of SSDLC
The Secure SDLC unifies this process and makes it a coherent program rather than a series of random, unconnected actions. There are typically six phases for an SSDLC as shown below.
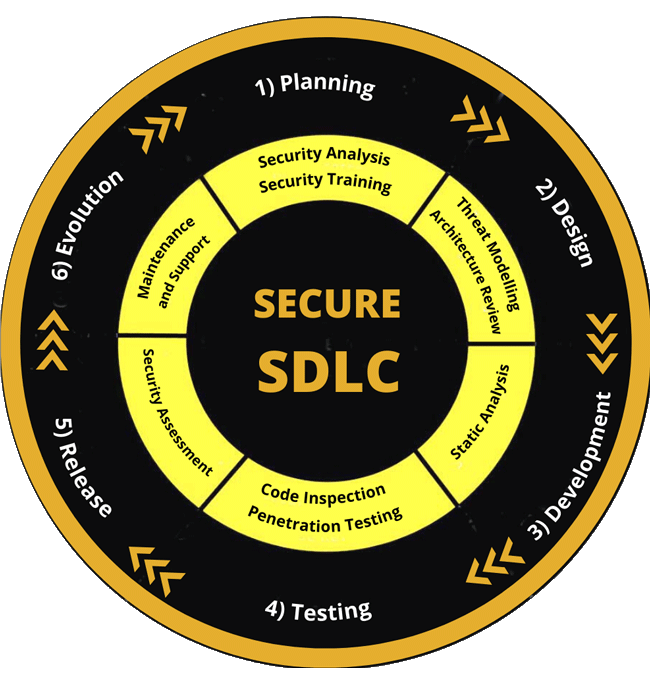
1) Planning
This is the first phase of the SDLC, different stakeholders from management, development teams, design teams or any relevant teams will plan, discuss and define the goals and requirements for the software projects.
Security Analysis
Security Analysis is performed to identify the possible risks connected with developing the software.
Security Training
Security Training is conducted to help a non-tech individual to have a better understanding of information security elements.
2) Design
In this phase, developers and other relevant teams will study the requirements and develop the design blueprints of the software.
Architecture Review
The developers will choose and review the right architecture for the software development. Each architecture needs a deep analysis of the technology profile, and the attack surface and ensures it’s not vulnerable by design.
Threat Modelling
This involves understanding and identifying the specific threats by mapping the assets and protection in place. Then creating specific controls to handle those threats.
3) Development
This is the development phase where developers begin to start building the software.
Static Analysis
In Static Code Analysis, you’re using the white box security testing method to examine the source code of the software.
4) Testing
The testing phase is done for quality assurance and to ensure no significant code errors in the software.
Code Inspection
Using automated and manual ways to identify easy-to-spot code errors and critical vulnerabilities.
Penetration Testing
Hack the software like how real hackers will do to identify and fix critical vulnerabilities before releasing the software to the public.
5) Release
In the release phase, the software is launched to the public and can be used by users.
Security Assessment
Developers conduct additional evaluation and validation testing on the whole software project during the Security Assessment step to ensure the software is ready for release.
6) Evolution
In this phase, the developers maintain the usability of the software and provide support to fix minor issues.
Maintenance and support
The battle for a stable, secure and reliable system is always needed whereas discovering the vulnerabilities and mitigating security threats is a constant effort to maintain security.

Benefits of Secure SDLC
1) Software is more secure
Focusing on security throughout the entire software development lifecycle results in software that is more secure than ever.
2) Demonstrating a continuous commitment to security
The goal is to provide all the stakeholders that can influence application security with the training, awareness and resources they need to be successful.
This will enable all interested parties such as project managers, development managers, application developers, server configuration, release management, quality assurance teams and others to become committed and aware of security considerations.
3) Identify vulnerabilities early in the process
SSDLC is a systematic process that will bake security processes into the development lifecycle, rather than bolting them in at the end of the lifecycle. This will help detect security vulnerabilities for each phase ensuring the software will be less prone to errors and security risks which will reduce business risks for the organization.
4) Reduce costs
It’s much easier and more cost-effective to design security from the start than to try and retrofit security into existing applications and APIs. Furthermore, it cost much less to fix security vulnerabilities in the initial stage than in later stages of the SDLC.

