Intelligence-led Penetration Testing
Intelligence-led pentesting uses threat intelligence to collect, analyze and gather business and technical overview about particular organizations that will use to perform an intelligence-led penetration test.

Condition Zebra’s Intelligence-led Penetration Testing Process
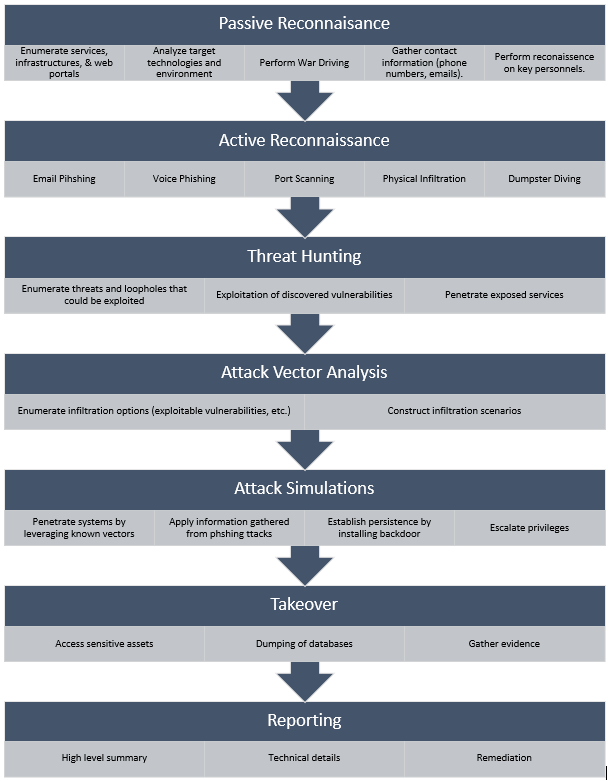
Passive Reconnaissance
Gather any information about the target by using techniques such as war driving, information gathering, and etc. Services information, contacts, and infrastructure plans are enumerated for further use. Human resources (personnel) are also targeted.
Active Reconnaissance
Actively probe infrastructure, services and key personnel of the target to obtain sensitive and sometimes critical information to aid the infiltration attempts in later stages. Techniques used include email phishing, voice phishing, port scanning, physical Infiltration, dumpster diving.
Threat Hunting
Discover vulnerabilities and establish attack vectors by enumerating weaknesses and loopholes (in systems and practices) and penetration testing on the enumerated targets gathered in previous stages. The successful discovery of multiple weak points allows for more elaborate infiltrations.
Attack Vector Analysis
Analyze available options (vectors) and deduce the best course of actions for successful infiltration, leveraging every piece of information gathered thus far.
Attack Simulations
Simulate real-life attacks by putting the infiltration plans into action. Successful infiltration will result in a takeover. The effectiveness of the target’s security measures and personnel will be assessed in this stage.
Takeover
Successful takeover results in compromise of all sensitive assets. Data are dumped from critical assets to demonstrate the extent of the potential damages.
Reporting
The final report includes organized information regarding the entire activity, sections such as the following are included:
- High-level summary
- Technical Details
- Proposed remediation
Benefits
EDR are typically deployed on endpoints and uses various techniques such as machine learning, behavioral analysis and threat intelligence to detect suspicious activities.
Access to intelligence data
Get access to intelligence collected about your organization which shows information about potential threat actors along with their tactics and techniques.
Gain insights
Gain insights into your organization’s resilience capabilities against real-world threat scenarios.
Improve Incident response capabilities
Get to measure your organization and whether it has appropriate countermeasures and responses to detect and avert cyberattacks.
Contact Us
+603-7665 2021
Level 3-10, Block F, Phileo Damansara 1, 46350 Petaling Jaya, Selangor, MALAYSIA.
Monday-Friday: 9am – 6pm
Schedule a FREE CONSULTATION to learn more about Condition Zebra Endpoint Detection & Response – Schedule Appointment or Whatsapp
