Introduction
Spear phishing is one of the sneakiest and most dangerous online scams today. Unlike regular phishing, which blasts out generic emails to thousands of people, spear phishing is personal. Attackers carefully craft messages to target specific individuals or companies, making them much harder to spot. Cybercriminals are getting smarter, so it’s crucial to understand how these attacks work, recognize the warning signs, and take steps to stay safe.
What is Spear Phishing?
Spear phishing is a type of online scam where attackers send realistic-looking emails or messages to trick someone into giving up sensitive information, downloading malware, or sending money. Unlike mass phishing emails, these attacks use personal details—like names, job titles, or recent activities—to make the messages feel real. This tactic plays on trust and familiarity, making even security-conscious people fall for them.
Spear Phishing vs. Regular Phishing
Phishing and spear phishing are similar, but there’s a big difference:
- Phishing: Generic emails sent to thousands of people, often pretending to be from banks, social media platforms, or well-known companies. The goal is to trick as many people as possible into clicking a bad link.
- Spear Phishing: Targeted attacks aimed at specific individuals or organisations. Attackers gather information beforehand to create a convincing and personalised message. Because it feels more legitimate, people are more likely to fall for it.
Since spear phishing is more personal and well-crafted, it has a much higher success rate than regular phishing scams.
The Evolution of Spear Phishing
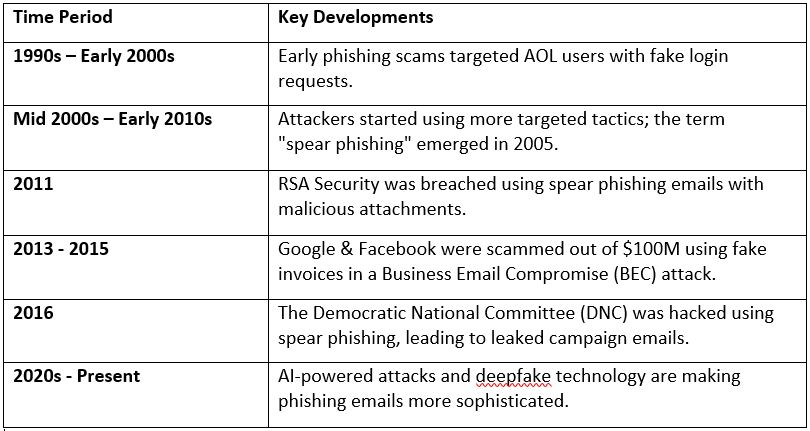
Early Phishing Scams (1990s – Early 2000s)
Hackers first started using phishing in the mid-90s to steal AOL login credentials. These scams relied on simple tricks to get users to reveal their passwords.
The Rise of Targeted Attacks (Mid-2000s – Early 2010s)
As people became more aware of phishing, attackers shifted to more targeted approaches. The term “spear phishing” was first used in 2005, and by 2006, U.S. military officials had already become victims.
High-Profile Cyber Attacks (2010s – Present)
- 2011: The RSA Security Breach—hackers used spear phishing emails with fake attachments to infiltrate the cybersecurity company RSA.
- 2013-2015: A hacker tricked Google and Facebook into wiring over $100M through fake invoices in a Business Email Compromise (BEC) scam.
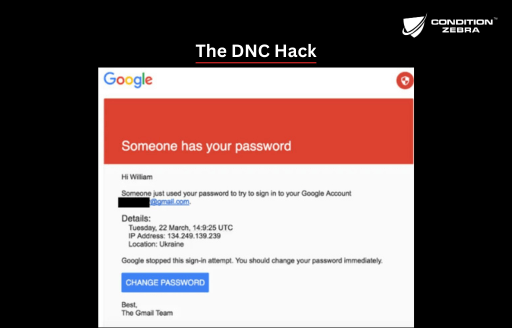
- 2016: The Democratic National Committee (DNC) was hacked using spear phishing emails, leading to leaked emails during the U.S. election.
AI-Powered Attacks (2020s – Future)
Cybercriminals now use AI to make their attacks even more convincing. Business Email Compromise (BEC) scams have skyrocketed, and deepfake technology is emerging as a new threat, although its use in phishing is still limited.
How Spear Phishing Works
- Picking a Target – Attackers choose high-value individuals like executives, HR personnel, or finance employees.
- Gathering Information – They collect personal details from social media, company websites, or previous data breaches.
- Launching the Attack – The attacker sends a highly personalized email with malicious links, fake login pages, or requests for sensitive information.
- Stealing Data or Money – If the victim falls for it, attackers gain access to private information, install malware, or steal funds.
Who is at Risk?
- Executives – They have authority and access to sensitive company information.
- HR & Finance Teams – They handle employee data and financial transactions.
- IT Administrators – If compromised, attackers can access entire networks.
- Healthcare & Government Employees – High-value targets for espionage and ransomware attacks.
Real-World Spear Phishing Cases
- Google & Facebook’s $100M Scam: A hacker impersonated a supplier and tricked both companies into wiring millions to fraudulent accounts.
- The DNC Email Hack: Attackers used fake emails to steal login credentials and access sensitive campaign emails.
- CEO Fraud & BEC Scams: Criminals impersonated CEOs and instructed finance teams to transfer millions to fake accounts.
- Recent 2023-2024 Cases: Companies have reported AI-powered spear phishing attacks that mimic executives’ voices and writing styles.
How to Spot a Spear Phishing Email
- Urgent requests that pressure you to act quickly.
- Email addresses that don’t match official domains.
- Requests for passwords or financial transactions.
- Suspicious links or unexpected attachments.
How to Protect Yourself and Your Organization
For Individuals:
- ✅ Always verify the sender’s identity.
- ✅ Hover over links before clicking to check where they lead.
- ✅ Enable multi-factor authentication (MFA) for extra security.
For Companies:
- ✅ Train employees to recognize phishing attempts.
- ✅ Use email security filters to block suspicious messages.
- ✅ Implement strict financial verification policies.
- ✅ Conduct phishing simulations to test employee awareness.
Advanced Techniques Used in Spear Phishing
- Social Engineering Manipulation: Exploiting trust and authority to trick victims.
- Man-in-the-Middle Attacks: Intercepting email communications to modify messages.
- Zero-Day Exploits: Using unknown software vulnerabilities to deliver malware.
Response Plan for a Spear Phishing Attack
- Report the Incident – Immediately inform IT and security teams.
- Change Passwords – If you clicked on a malicious link, update all relevant credentials.
- Check Financial Transactions – Ensure no fraudulent transactions have been made.
- Scan for Malware – Run a security check on your device.
- Educate Employees – Review security policies and reinforce best practices.
The Future of Spear Phishing
- AI-Powered Attacks – Attackers are using AI to craft even more convincing emails.
- Deepfake Technology – While still emerging, deepfake voice and video scams could become a serious threat.
- Stronger Cyber Defenses – Businesses are investing in better security solutions to combat phishing.
Conclusion
Spear phishing is getting smarter, but so can you. By staying aware of the latest tactics, double-checking emails, and using strong security measures, you can keep yourself and your organization safe. The best defense against spear phishing is knowledge—so stay informed and stay secure!
Condition Zebra is a cybersecurity company with over 15 years of experience, offering advanced cybersecurity solutions and training to companies and government institutions.
We specialise in tailor-made cybersecurity solutions designed specifically to mitigate clients’ operational, legal, and financial threats using our specialised services, the main one includes:
Managed Security Operations Centre (SOC) Monitoring Service
Information Security Awareness Program
Source:
Firewall Times: Spear Phishing Examples

