Hackers use this tactic, known as “email phishing,” which is a type of cyberattack where a hacker uses emails by posing as a trusted business to trick recipients into giving out personal information, and bank details, and clicking on malicious links.
Furthermore, these emails encourage recipients to confirm personal information, bank details, etc. by clicking on a link that directs them to a page. Also, a 2022 data breach investigation report states that 70% of breaches that contain elements of a social engineering component relate back to phishing (Verizon, 2018).
Employees are the first point of contact in a company and are often identified as the weakest link in the security chain. This makes it crucial for employees to understand how to spot email phishing scams and how to respond to them if they encounter one. According to Sobers (2018), it took a targeted employee from a well-known company approximately 16 minutes to click on a phishing link.
How to Spot Phishing Emails?
1) Emails Sent With a Sense of Urgency using fear Tactics
Huddleston (2022), explains that an email with a sense of urgency in the subject line that entices you to open it is most likely a phishing email.
For example:
a) Payment Declined — Update Required Immediately!
b) Password Check is Required Immediately
c) Account Suspension
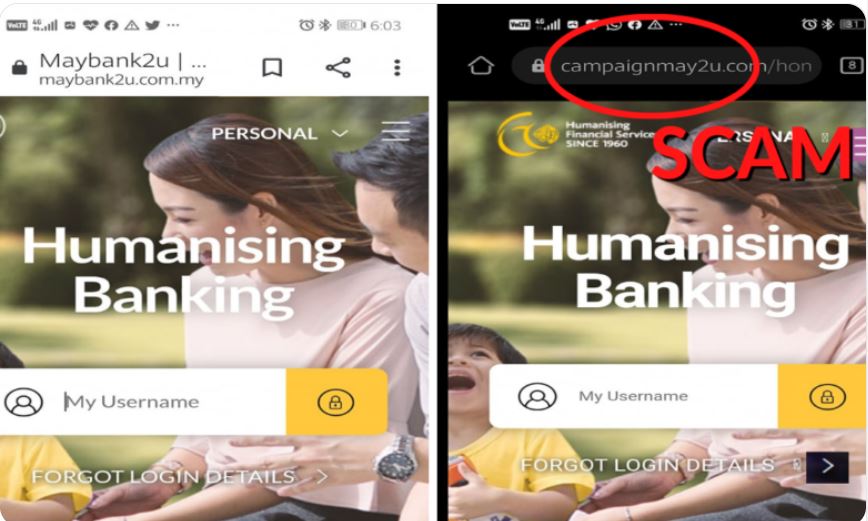
2) Modified or misspelt domain name.
Another indicator that strongly suggests phishing scams is the use of misspellings in domain names (Ellis, 2022). In addition, anyone can purchase a domain name from a registrar, which is concerning. Further, Irwin (2022) demonstrates the numerous ways to produce email addresses that are identical to the one that is being faked, even though every domain name must be unique.
To illustrate, Maybank Malaysia (2022) publicly issued a statement about phishing scams, warning customers of the new techniques hackers are using to steal their accounts and bank details. The official Maybank has demonstrated the ways in which hackers operate. They begin by prompting customers to reveal their banking details through a systematic re-verification method.
In light of the issue, Maybank Malaysia reminded their customers that if they encounter messages through WhatsApp, SMS, or email from Maybank urging their customers to log in and update their Maybank2u account, it’s likely bogus and a phishing attempt.
3) Emails that have an unfamiliar greeting or salutation
Typically, emails sent and received between coworkers begin with a casual salutation. Furthermore, any correspondence that begins with ‘Dear’ or includes words and phrases not often used in casual conversation that are unfamiliar with the office mannerisms should already be a giveaway to raise suspicion (Ellis, 2022).
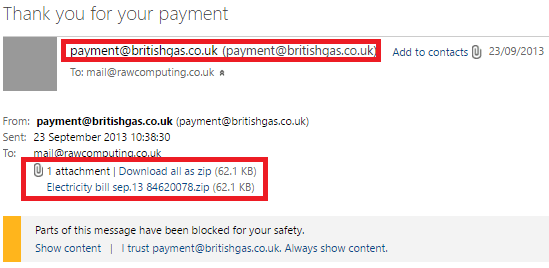
4) Emails that Contain Suspicious Attachments
Collaboration services like SharePoint, OneDrive, or Dropbox are currently used for the majority of file sharing linked to work. Internal emails with attachments, according to Sobers (2018), should always be viewed with suspicion, especially if they have an unknown extension or are frequently linked to malware extensions (.zip,.exe,.scr, etc.).
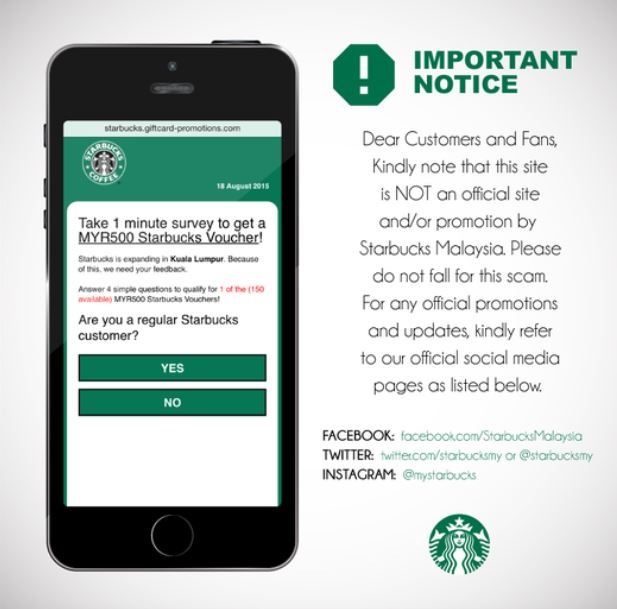
5) Emails that just seem too good to be true
In emails that appear to be too good to be true, the sender entices the receiver to open an attachment or click on a link by promising a prize of some sort (Sobers, 2018). Therefore, there is a high chance that it is a phishing email if the sender of the email is unknown or if the recipient has never initiated contact with the sender before.
A classic example of a too-good-to-be-true situation: in 2015, Starbucks Malaysia had to publish an official statement on their social media platforms to inform their customers of a bogus survey that promised them a RM 500 Starbucks voucher.
Dealing with email phishing scams
Phishing scams are usually emailed to a multitude of recipients all at once or in bulk. The attack typically targets those who share similar characteristics. These phishing scams are targeted at all known customers, suppliers, or employees of the company.
Hackers asking for your personal information is one of the most common indicators of a phishing scam, along with the use of generic greetings or none at all, misspelt subject lines and email addresses, deceptive hyperlinks, and links to odd websites.
1) Reporting phishing emails.
Users can report the phishing emails they receive by forwarding them to the company’s IT team or relevant authorities such as Cyber999, which is a cyber security incident response centre operated by MyCERT (Malaysia Computer Emergency Response Team).
2) IT Security Awareness Training
Training for heightened vigilance regarding safety in modern institutions is in dire need. Condition Zebra has formed a partnership with KnowBe4 in order to provide thousands of IT security training modules to increase the security awareness of employees. KnowBe4 provides the most comprehensive integrated security awareness training and simulated phishing platform, with tens of thousands of customers globally.
In order to effectively combat email phishing attacks, businesses are required to increase their level of vigilance by educating their employees (Irwin, 2018). This can be done by enrolling in IT Security Awareness Program to help employees better identify and potentially stop these attacks.
Your Preferred Cybersecurity Partner!
Condition Zebra is a CREST-certified and ISO 27001:2013 company that offers Professional Cybersecurity Solutions and Cybersecurity Training for SMEs in various industries, including Financial Services (Banks & Insurance), Government Ministries & Agencies, and Government-linked companies.
If you’re looking to leverage our expertise, that is to get the best solutions that demonstrate the highest levels of knowledge, skills, and competence, then reach out to us today!
How we can help:
1) Free Phishing Security Test
The purpose of this Free Phishing Security test is to provide a safe space for IT teams to implement email phishing simulations for all the employees in the company.
Find out what percentage of your employees are at risk and how many of your users are clicking on phishing links.
Click here for a Free Phishing Security Test
2) Train your users
Introducing, KnowBe4 Security Awareness Training Platform, the world’s largest library of security awareness training content, including interactive modules, videos, games, posters, and newsletters. Automated training campaigns with scheduled reminder emails
The significance of cybersecurity awareness training for employees cannot be overstated. If they are well taught and aware of the types of attacks they may face, they will know what action to take. This will protect them against any type of attack, regardless of its severity.
Click here to learn more about IT Security Awareness Program
References:
Ellis, D. (2022) 7 ways to recognize a phishing email: Email phishing examples, SecurityMetrics. SecurityMetrics. Available at: https://www.securitymetrics.com/blog/7-ways-recognize-phishing-email (Accessed: December 21, 2022).
Huddleston, B. (2022) Phishing with a Sense of Urgency, AppRiver. Available at: https://appriver.com/blog/in-progress-phishing-with-a-sense-of-urgency (Accessed: December 23, 2022).
Irwin, L. (2022) 5 ways to detect a phishing email: With examples, IT Governance UK Blog. Available at: https://www.itgovernance.co.uk/blog/5-ways-to-detect-a-phishing-email (Accessed: December 21, 2022).
Sobers, R. (2018) The anatomy of a phishing email, Varonis. Varonis. Available at: https://www.varonis.com/blog/spot-phishing-scam (Accessed: December 21, 2022).
Verizon, B. (2022) 2022 data breach investigations report, Verizon Business. Available at: https://www.verizon.com/business/en-gb/resources/reports/dbir/ (Accessed: December 21, 2022).
Share this:

