Ultimate Guide to Ransomware Attacks
This is the ultimate guide to ransomware attacks in Malaysia for 2022.
I will cover from the basics to advanced topics contributed by our cybersecurity experts.
Everything you need to know about ransomware will be explained in detail.
You will learn the steps to take to avoid getting infected.
AND…
In the case of infection, what critical steps you should take.
Let’s dive in.
1. Ransomware Overview
In this chapter, I’ll answer the question: “What Is Ransomware?”.
I’ll also show you how does a Ransomware infection occur.
Let’s get started.
What Is Ransomware?
Ransomware is a type of malware that prevents users from accessing their data on a computer by locking the file systems or computer screens.
It then attempts to prompt a ransom note on the computer asking the victims to pay in the form of digital currency like Bitcoin to restore access to their data and computers.
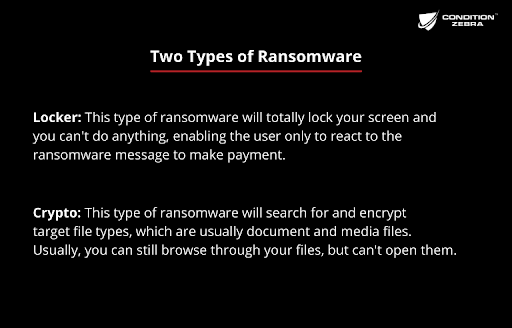
Two types of ransomware: Locker and Crypto.
What does ransomware do?
Most ransomware today restricts access to data on a victim’s computer by encrypting MFT, Main File Table. Once the Main File Table is encrypted, all the executable files will not be able to run.
It uses known encryption algorithms like RSA or RC4, or custom encryption.
Ransomware like Cerber and Locky will search and encrypt important file types, such as documents and media files like photos and videos.
When the encryption is complete, the malware leaves a ransom note, which can be a text, image, or HTML file with instructions to pay a ransom in order to recover files.
How does a ransomware infection occur?
Ransomware infection usually can begin with any of the following vectors:
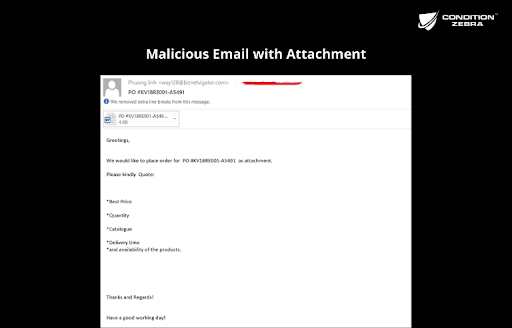
a) Malicious email
Email messages with an attachment trick you to download it that carries downloader trojans, which attempt to install ransomware.
b) Malicious website or fake website
If you accidentally visit a website that has been hacked and infected with an exploit kit, you can download the ransomware file on your computer automatically without you knowing about it.
A fake website is made to imitate a legitimate website. When the user clicks a link on the website it will download the trojans, which attempt to install ransomware.
How does ransomware infect in network share drive?
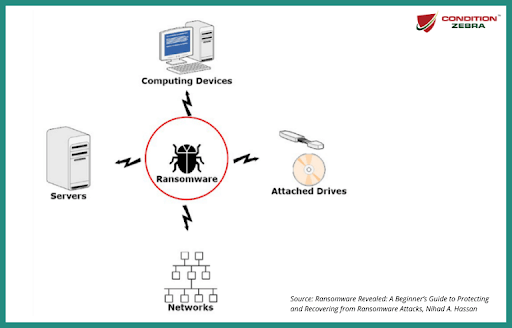
The latest ransomware has worm-like characteristics that enable them to infect other computers in the network. For example, Spora ransomware duplicates itself in network shares.
Wannacry ransomware, use the Eternal Blue exploit that use Server Message Block (SMB) vulnerability CVE-2017-0144 to attack and spread to other computers in a network.
In the WannaCry ransomware incident, the use of the Eternal Blue exploit was widespread. Thus, all the computers in the same network are going to get infected.
It’s very hard to stop the infection because cybercriminals use social engineering methods that will persuade you to click on the link.
What are ransomware cases that have been reported in Malaysia?
That’s what I’m going to cover in the next chapter.
Keep reading…
2. Ransomware cases in Malaysia
In this chapter, we will look at the popular cases of ransomware attacks in Malaysia to educate and provide security awareness to everyone.
As we entered the year 2022, cybersecurity remains a critical issue for the world to combat. The past year since the pandemic saw cybercriminals launching ransomware attacks were rampant.
Ransomware is identified as one of the top cyber threats.
The top industries that experience the most ransomware incidents are government, healthcare and manufacturing.
Most SMEs are reluctant to admit that they have experienced ransomware attacks and some want to make it confidential as this affects the reputation of the company.
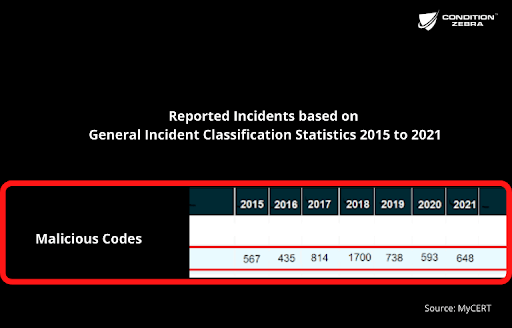
Since ransomware falls under the category of malicious codes. Check out the total number of malicious codes attacks from 2015 to 2021 as reported by the Malaysia Computer Emergency Response Team (MyCERT).
2021
According to Malaysia Computer Emergency Response Team (MyCERT), a total of 648 cases of malicious code (ransomware falls under this category) were reported in 2021.
Malaysia still is a hot target with cybercriminals with 30% of respondents mentioning being hit by ransomware as reported in The State of Ransomware 2021, SOPHOS.
Below are some of the headlines in the news about the ransomware attack.
1) Vintage shoe seller
Wan Irfayuim Azim was hit by ransomware, a vintage shoe seller, who went viral after selling a converse vintage shoe for RM40,800.
His computer was hit by ransomware and all files cannot be opened. A ransom note that instructs him to pay USD$960 (RM4000) is displayed whenever he tries to access one of the folders on his computer.
(New Straits Times, 2021)
2) Malaysian Employers Federation (MEF)
The Malaysian Employers Federation (MEF) computer servers were down for three days and followed by a ransomware incident that targeted its encrypted accounting data.
(The Star, 2021)
3) Exabyte
Exabyte, Malaysian Web Hosting company hit by ransomware.
(Lowyat, 2021)
4) Axa Insurance
French insurance company – Axa’s Asian operations (including Malaysia) were affected by Ransomware.
(Lowyat, 2021)
2020
According to Malaysia Computer Emergency Response Team (MyCERT), a total of 593 cases of malicious code (ransomware falls under this category) were reported in 2020.
2019
According to Malaysia Computer Emergency Response Team (MyCERT), a total of 738 cases of malicious code (ransomware falls under this category) were reported in 2019.
Below are two prominent companies making headlines in the news about the ransomware attack.
5) CIMB Bank
CIMB’s systems were hit by ransomware. (Pokde.net, 2019)
6) POS Malaysia
POS Malaysia possibility of ransomware attack. (Pokde.net, 2019)
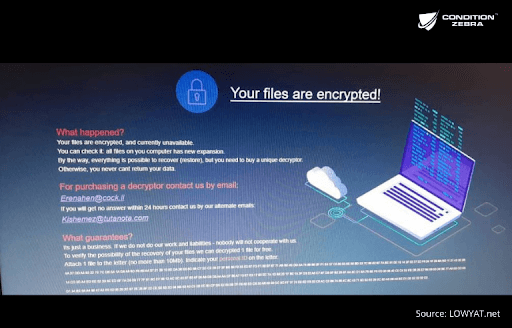
2018
According to Malaysia Computer Emergency Response Team (MyCERT), a total of 1700 cases of malicious code (ransomware falls under this category) were reported in 2018.
The year where we saw more ransomware attacks, fuelled by Ransomware-as-a-Service (RaaS) and amplified by the resurgence of worms.
Ransomware-as-a-service (RaaS) is the malevolent equivalent of software-as-a-service (SaaS) provided by hackers to sell their malicious ransomware platform tool to less sophisticated cybercriminals.
7) Media Prima ransomware attack that makes the news.
Media Prima ransomware case serves as a reminder for other companies.
This attack prevents the use of its in-house email. Ransomware attackers demanded Media Prima to pay 1,000 bitcoins to allow its staff access to the company’s email system.
(Digital News Asia, 2018)
2017
According to Malaysia Computer Emergency Response Team (MyCERT), a total of 1700 cases of malicious code (ransomware falls under this category) were reported in 2017.
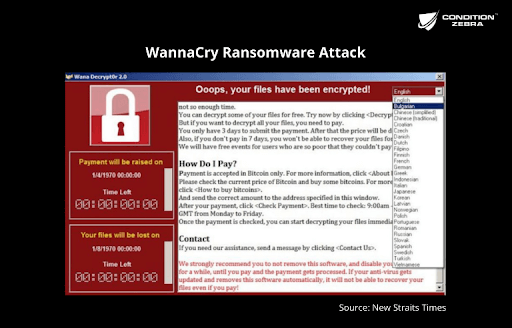
This is the time WannaCry and Petya ransomware outbreaks happen.
Ransomware attacks are among 2017’s biggest cyber incidents (WIRED, 2017).

News report about WannaCry ransomware.
8) An academic institution hit by ransomware
An academic institution in Malaysia has been hit by the WannaCry ransomware. This malware took control of computer or network systems and asked victims to pay a total of US$300 (RM1200) in Bitcoin digital currency to restore access to their systems.
(New Straits Times, 2017)
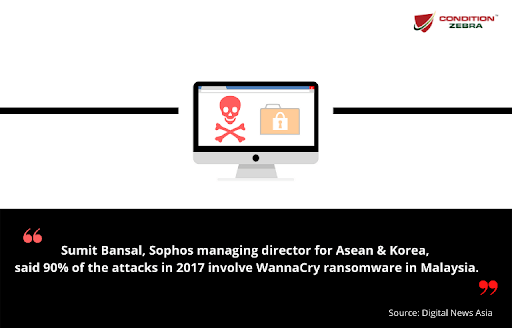
9) More Ransomware Cases were detected in Malaysia.
16 cases of WannaCry ransomware were reported. Probably there are more unreported cases. Affected companies include an entertainment outlet, maid agency and an investment firm.
(The Malaysian Reserve, 2017)
2016
According to Malaysia Computer Emergency Response Team (MyCERT), a total of 435 cases of malicious code (ransomware falls under this category) were reported in 2016.
According to Symantec Corporation, Malaysia ranks 47th globally, and 12th in the Asia Pacific and Japan region, in terms of ransomware attacks in 2016

2015
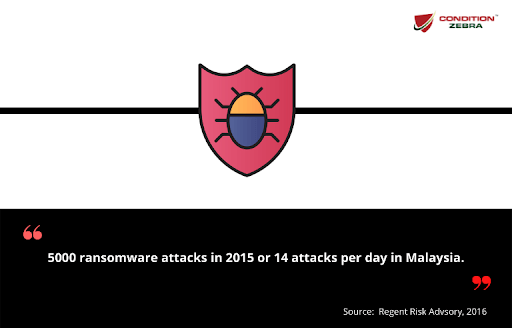
According to Malaysia Computer Emergency Response Team (MyCERT), a total of 567 cases of malicious code (ransomware falls under this category) were reported in 2015.
5000 ransomware attacks or 14 attacks per day in 2015. (Regent Risk Advisory, 2016).
With all the ransomware attacks that have been reported over the years, the overall impact for the affected companies is downtime, work hours, device cost, network cost, lost opportunities, and ransom payment.
You might be wondering:
So how do I recover from ransomware?
That’s what I’m going to cover in the next chapter.
Keep reading…
3. Ransomware Recovery
In this chapter, we will look at two methods of ransomware removal that will provide solutions to eliminate and remove it from infected computers.
Both of these methods work for Windows operating system like:
- Windows 7
- Windows 8.1
- Windows 10
When you first encounter ransomware screen popups like below. The first step you must take is to turn your computer off or unplug it from your network. This ensures no other computers get infected.
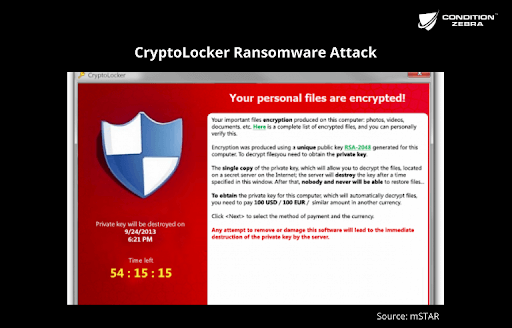
Method 1
In this method, we will run Microsoft Safety Scanner in Safe Mode which will automatically detect and eliminate the ransomware from your Windows operating system.
Step 1: Download a copy of the Microsoft Safety Scanner using a clean, non-infected PC.
Step 2: Copy the downloaded file to a blank USB drive or CD.
Step 3: Insert the blank USB drive or CD and restart your infected PC in Safe Mode.
Step 4: When you’re in safe mode, run the Microsoft Safety Scanner.
Method 2
In this method, we will download Windows Defender Offline from the official Microsoft website. This tool will be used to detect and remove the ransomware from your Windows operating system.
Step 1: Download a copy of Windows Defender Offline using a clean, non-infected PC.
Step 2: Copy the downloaded file to a blank USB drive or CD.
Step 3: Insert the blank USB drive or CD and restart the PC.
Step 4: When you run Windows Defender Offline, you will be prompted to install the tool on the USB drive or CD.
Step 5: Once Windows Defender Online is installed on the removal media, insert it into the infected PC, then restart in safe mode. You will then be prompted to run the Windows Defender Online tool.
After the removal process is completed, make sure you format and do a clean reinstall of your Windows operating system with the latest patch
Then restore from backup (if any backup is available).
You might be wondering:
Prevention is better than cure.
So how do I prevent ransomware?
That’s what I’m going to cover in the next chapter.
Keep reading…
4. Ransomware Prevention
According to Wong Joon Hoog, Country Manager, Sophos Malaysia.
“The best way to prevent cyberattacks, especially ransomware is to prepare in advance. Most organisations realize the need for an incident response plan, only after they become victims of cyberattacks.”
Here we give you six strategies you can use in your incident response plan. All these strategies can be used by an individual or company to protect its devices like computers or networks from ransomware.
How do I protect my company’s network and computer from ransomware?
- Back up your files
Back up your most important files and data regularly using Cloud storage and External hard disk. In the case of a ransomware attack, you will still have the means to access your data from the backup. - Install anti-ransomware software. Suggested softwares as below:
- Device Guard
Device Guard is a new feature of Windows 10 Enterprise.
Use Device Guard to lock down devices and provide kernel-level virtualization-based security, allowing only trusted applications to run. This can effectively prevent ransomware and other dangerous software from executing. - Microsoft Edge browser
When you use Microsoft Edge browser, its Microsoft Defender SmartScreen can identify reported phishing and malware websites. This protects against ransomware by reported phishing and malware websites. This ensures protection against ransomware by stopping exploit kits from running and executing ransomware. - Microsoft Safety Scanner
Microsoft Safety Scanner is a scan tool that is used for malware detection and removal from Windows computers. - Enable Windows Defender
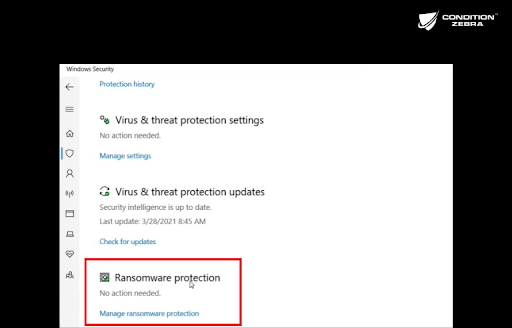
Windows Defender is built into Windows 10 and when enabled, provides real-time protection against ransomware as well as the exploit kits and trojan downloaders that install them. - Using Ransomware Protection
This Ransomware Protection is built into Windows 10 and can be activated easily by going to the Windows Security section then Virus & Threat protection section. Click the manage ransomware protection to go to the page.
3. Using Anti-virus software and keep them updated
Antivirus software from Kaspersky, trend micro, Malwarebytes and others provides real-time protection against threats. Also keep Windows Defender, Anti-virus and most importantly your operating systems – Windows or Linux updated to get the latest protection.
4. Use 24/7 Security Operations Centre
If you’re an enterprise and have a budget then allow your company to pair your anti-ransomware technology with a 24/7 Security Operations Centre that monitors, analyzes and protect your organization from cyber-attacks.
5. Train your employees.

Cybersecurity awareness training for employees is very important to provide awareness of ransomware.
Start by giving the right knowledge to your employees so they’re able to protect your organisation by remaining vigilant and careful in using computers, the Internet and its applications.
In the long run, you will save money and your reputation by being protected
6. Secure your network.
Deploy layered protection across as many endpoints on your network as possible.
Most of these attacks rely on your connection to spread in a network, so necessary protection is vital before it goes viral.
Let’s say you just want to pay the ransom and be done with this mess.
Read the next chapter to find out whether should you pay or not.
Let’s move on…
5. Ransomware Dilemma: To pay or not
Should I pay the ransom to get my files back?
We suggest don’t pay the money because it does not guarantee that you will be able to decrypt and get your system or files back.
In some cases, paying the ransom can make you a target for more malware attacks.
Inform and report the case of ransomware, along with your affected public IP address to your ISP (Internet Service Provider)
6. Conclusion
Our team of cybersecurity experts is available that give professional advice regarding ransomware attacks or any other cybersecurity incidents.
Report to us
Condition Zebra have achieved ISO 27001:2013 and our Penetration Testing service is recognized as an accredited service by Accreditation body CREST.
We utilize a unique strategy of combining key technologies with expertise in Information Security and Risk Management services to help mitigate operational, legal and financial threats for our clients.
Report ransomware or any cybersecurity incidents to us via the contact us form on Contact Us page.
OR
You may also be able to reach us via Whatsapp.
References
- How to Stay Protected Against Ransomware – A Sophos Whitepaper, 2019
- 2016 Norton Cyber Security Insights Report
- The State of Ransomware 2021, SOPHOS
- csoonline.com/article/2123316/a-layman-s-glossary-of-malware-terms.html
- regentsriskadvisory.com/ransomware-attacks-surge-in-malaysia
- mstar.com.my/lokal/semasa/2015/01/31/cybersecurity
- Ransomware Revealed: A Beginner’s Guide to Protecting and Recovering from Ransomware Attacks, Nihad A. Hassan
- MyCERT: Malaysia Computer Emergency Response Team
- themalaysianreserve.com/2017/05/18/more-ransomware-cases-detected-in-malaysia-unreported-cases-likely/
- udemy.com/course/the-complete-guidance-of-ransomware
- www.digitalnewsasia.com/malaysian-companies-ripe-targets-ransomware-trend-micro
- www.thesundaily.my/home/tackling-the-ransomware-risk-to-enterprises-in-malaysia-FC8631557
- goingplaces.malaysiaairlines.com/tm-one-cydec-randomware-cybersecurity-malaysia/

